Collecting personal information is a normal part of doing business. Whether it’s from customers, employees, or vendors, most businesses handle sensitive data that needs to be protected.
Once this information is collected, it’s a business’s responsibility to keep it safe, and complying with data privacy laws is one of the best ways to do it.
These regulations are designed to protect both consumers and businesses, but figuring out which rules apply to you can be challenging. With federal, state, and local governments all issuing their own requirements, navigating privacy laws can quickly become complicated, especially when the rules overlap or conflict.
Failing to meet these requirements doesn’t just put your customers personal data at risk, it can also result in fines, lawsuits, and other legal penalties. Even more concerning, a data breach can damage a business’s reputation and erode trust, sometimes with long-lasting effects.
Understanding what data is protected and the laws that regulate it makes it easier to protect your sensitive data and your business. In this article, we’ll discuss the most important data privacy laws that businesses need to be aware of, as well as offer some basic tips to make staying compliant with them a bit easier.
Note: This article provides general information only and should not be construed as legal advice.
What Types of Personal Information Are Considered Sensitive?
In order to comply with data privacy laws, you’ll need to understand what qualifies as sensitive information. Most privacy regulations focus on two main categories of data:
Personally identifiable information (PII) includes any details that can be traced back to an individual’s identity. This covers names, addresses, social security numbers, and financial data like credit card information.
Personal health information (PHI) includes health-related details, such as patient charts, insurance information, and medical history. These records are considered especially sensitive and are strictly regulated to ensure they remain secure.
Protecting sensitive data, whether it’s PII or PHI, helps prevent identity theft, discrimination, and financial crimes. That’s why so much effort goes into keeping this information secure.
For most businesses, employment records are one of the largest sources of PII. From job applications and payroll information to benefits records and tax forms, businesses are required to store a lot of sensitive data about their employees. These records have strict retention policies, meaning you are required to keep them on file for an extended period, so it is important to have the necessary protocols in place to ensure these records are secure at all times.
How Data Privacy Laws Are Structured in the U.S.
Unlike many other countries, the United States does not have a single, comprehensive law to protect data privacy. Instead, privacy protections are enforced through a mix of federal and state-level regulations, each focused on specific types of data or industries.
While interest in stronger privacy protections continues to grow globally, the U.S. has taken a more decentralized approach. Part of the reason is that there’s no dedicated federal agency responsible for overseeing data privacy. Instead, enforcement falls to multiple regulatory bodies, each tasked with handling different aspects of data protection.
This fragmented structure means businesses need to pay close attention to which laws apply to their industry and the types of data they collect.
In the next section, we’ll break down some of the most important privacy laws businesses should be aware of.
US Privacy Act of 1974
The US Privacy Act of 1974 was the first major privacy law passed in the United States, taking effect on September 27, 1975.
Often referred to as simply “The Privacy Act,” it was created in response to growing concerns about how computerized databases might impact personal privacy. The law regulates how federal agencies collect, store, and share personal information, giving individuals the right to access and correct their own records.
Under the Privacy Act, federal agencies are prohibited from sharing any personal records without written consent, unless the disclosure falls under one of twelve exceptions outlined in the law.
Protections Provided By the Privacy Act
The Privacy Act gives individuals several rights when it comes to their personal information.
Access to Records allows U.S. citizens to request access to personal data held by government agencies and correct any errors they find. This ensures individuals have some control over the accuracy of their information.
Minimal Data Collection requirements limit agencies to collecting only the information necessary to perform their duties. This reduces the risk of over-collection and helps protect personal privacy.
Restricted Access rules ensure that personal data can only be accessed by employees who need it to perform their jobs. By enforcing a “need-to-know” policy, the law minimizes unnecessary exposure to sensitive information.
Limits on Sharing prevent agencies from disclosing data to other organizations unless specific legal exceptions apply. This safeguard ensures information isn’t shared more widely than necessary.
Who Must Comply?
The Privacy Act applies to any federal agency, contractor, or entity that maintains records linked to personal identifiers, such as names, addresses, or Social Security numbers. These rules are relevant for government agencies and businesses working under federal contracts.
Compliance Tips
Businesses and contractors covered by the Privacy Act should maintain an up-to-date inventory of systems containing personal data. Keeping clear documentation of how records are stored and accessed can help demonstrate compliance.
It’s also important to give individuals an easy way to review and correct their records. Having a clear process for handling these requests shows transparency and accountability.
Finally, personal data should only be used for lawful and well-defined purposes. Businesses must be upfront about how data is collected, stored, and shared to build trust and meet legal requirements.
Gramm-Leach-Bliley Act (GLBA)
The Gramm-Leach-Bliley Act (GLBA) was enacted in 1999 to protect consumers’ financial information. It applies to any business or institution that offers financial products, including loans, financial or investment advice, and insurance. Under this law, businesses must explain their data-sharing practices to customers.
The GLBA does not restrict how companies can use the data they collect. Instead, it sets requirements for disclosing these practices beforehand, ensuring customers are informed about how their information may be shared.
Protections Provided By the GLBA
The Gramm-Leach-Bliley Act (GLBA) establishes several protections to safeguard consumers’ personal and financial information.
The Financial Privacy Rule requires financial institutions to inform customers about how their data is collected, shared, and protected. Customers must also have the option to opt out of certain data-sharing practices, giving them more control over their personal information.
The Safeguards Rule mandates that businesses create a written security plan to protect sensitive information. This plan must address potential risks, outline procedures for securing data, and include training for employees to follow these safeguards.
The Pretexting Protection provision prevents unauthorized access to private information through deceptive methods like impersonation or social engineering. These rules help reduce the risk of fraud and identity theft.
Who Must Comply?
The GLBA applies to financial institutions, including banks, insurance companies, mortgage brokers, and investment firms. It also covers businesses that handle financial data, such as tax preparation services, credit counselors, and debt collectors.
Since the law applies to any business involved in financial services, organizations must ensure data is protected at every stage, whether it’s being collected, stored, or shared with third parties.
Compliance Tips
Assess Risks: Regularly evaluate how customer data is collected, stored, and accessed to identify potential security gaps, both physical and digital.
Develop a Security Plan: Create detailed policies for protecting sensitive information and train employees to follow these protocols. Include steps for responding to data breaches or other security incidents.
Review Third-Party Vendors: Confirm that service providers with access to customer data meet GLBA security standards. Contracts should clearly define data protection responsibilities.
The Fair Credit Reporting Act
The Fair Credit Reporting Act (FCRA) was passed in 1970 as part of the Federal Consumer Credit Protection Act to regulate how consumer reporting agencies handle personal data. Its primary purpose is to protect the information collected in consumer reports and ensure it is used appropriately.
The FCRA limits how and when sensitive information in a consumer report can be accessed or shared. It also requires lenders, employers, and insurers to notify individuals if information in their credit file is used to deny a job application, loan, or insurance policy.
Beyond credit reports, the FCRA also applies to criminal and civil records, lawsuits, reference checks, and other data obtained through consumer reporting agencies.
Protections Provided By FCRA
The Gramm-Leach-Bliley Act (GLBA) includes several rules designed to protect consumers’ personal and financial information.
The Financial Privacy Rule requires financial institutions to explain how they collect, share, and protect customer data. Businesses must also give customers the option to opt out of certain data-sharing practices, allowing individuals more control over how their information is used.
The Safeguards Rule requires institutions to create a written security plan outlining how they will protect sensitive information. This plan must address both physical and digital threats to customer data and ensure staff are properly trained to follow security procedures.
The Pretexting Protection rule prohibits deceptive tactics like impersonation or social engineering to gain access to private information. This helps prevent fraud and identity theft.
Who Must Comply?
The GLBA applies to financial institutions of all sizes, including banks, insurance companies, mortgage brokers, and investment firms. It also covers businesses that handle consumer financial information, such as tax preparation services, debt collectors, and credit counselors.
Because these rules apply broadly to businesses involved in financial services, companies must take steps to ensure they’re protecting customer data at every stage—from collection to storage and disposal.
Compliance Tips
Assess Risks: Regularly review how customer data is collected, stored, and accessed to identify potential vulnerabilities, both physical and digital.
Develop a Security Plan: Create written policies for handling sensitive data and make sure employees are trained to follow them. Plans should also outline procedures for responding to data breaches.
Review Third-Party Vendors: Ensure any service providers with access to customer data follow security requirements under the GLBA. Contracts should clearly outline data protection expectations.
Fair and Accurate Credit Transactions Act
The Fair and Accurate Credit Transactions Act (FACTA) is an amendment to the Fair Credit Reporting Act (FCRA) that strengthens protections for consumers’ credit-related records.
One of its main provisions gives consumers access to one free credit report per year, along with details about how their credit score was calculated. FACTA also includes measures to help prevent identity theft, such as allowing consumers to place fraud alerts on their credit reports when suspicious activity is detected.
In addition to protecting credit information, FACTA sets specific rules for disposing of sensitive records. Any business that maintains or handles credit-related data must securely destroy outdated information to prevent unauthorized access.
Protections Provided By FACTA
While FACTA primarily targets credit reporting agencies, its disposal rules apply to nearly all businesses that collect, store, or use consumer information for business purposes.
Businesses are required to dispose of outdated records in a secure manner to prevent identity theft and unauthorized access. Many businesses choose to simplify the process of meeting these requirements by outsourcing document destruction to professional shredding services.
Who Must Comply?
FACTA applies to a wide range of businesses—not just credit reporting agencies. Any company that collects, stores, or uses consumer information for business purposes must comply with FACTA’s disposal rules.
This includes financial institutions, lenders, landlords, employers, and even small businesses that handle sensitive information as part of credit checks, background screenings, or payment processing.
Because the law covers both physical and electronic records, businesses are responsible for ensuring secure disposal methods regardless of how the information is stored.
Compliance Tips
Secure Disposal Methods: Shred or properly destroy physical documents containing consumer information before disposal.
Create a Document Destruction Policy: Develop clear policies that outline how and when records should be disposed of to meet FACTA’s disposal rule.
Leverage Digital Tools: Use document management systems with secure deletion features to permanently remove outdated electronic records after their retention period ends.
The Health Insurance Portability and Accountability Act
Passed in 1996, the Health Insurance Portability and Accountability Act (HIPAA) is a U.S. law that provides privacy standards to protect patients’ medical records and other health information from disclosure without a patient’s expressed consent.
HIPAA standardizes the processing and transmission of electronic healthcare information. It requires the organizations to implement safe electronic access to the patients’ health data, in a manner compliant with the privacy regulations set by the HHS.
Under HIPAA, records that contain any of the following 18 identifiers are considered to be protected health information:
- Names
- Geographic identifiers smaller than a state (street address, city, county, zip code etc.)
- Dates other than the year ex (birth date, admission date, discharge date)
- Phone numbers
- Fax numbers
- Email addresses
- Social Security numbers
- Medical record numbers
- Health plan beneficiary numbers
- Account numbers
- Certificate/license numbers
- Vehicle identifiers and serial numbers
- Device identifiers and serial numbers
- Web URLs
- IP addresses
- Bio-metric identifiers; including fingerprints and voice
- Full face photos
- Any other unique identifying number, characteristic, or codes
If these identifiers are removed from a record, it is considered to be “de-identified protected health information”, which is not covered by the HIPAA Privacy Rule.
*Note: New rules announced in 2024 enhance HIPAA’s protection of reproductive health records.
Protections Provided By HIPAA
HIPAA applicable to anyone providing treatment, payment, or operations in the healthcare field. It also applies to subcontractors or any other businesses that work alongside a medical practice who may handle sensitive health information.
Compliance Tips:
- Utilize document management systems that enforce access controls and audit trails.
- Engage in ongoing staff training to ensure HIPAA requirements are well understood.
- Conduct regular risk assessments to ensure all personal health information is securely managed.
Family Educational Rights and Privacy Act
The Family Educational Rights and Privacy Act (FERPA) is a federal law that protects the privacy of student education records. It gives parents certain rights over their child’s records, which transfer to the student once they turn 18 or enroll in college.
FERPA ensures that parents and eligible students have the right to inspect and review education records at any time. It also limits how schools can share this information, requiring written consent before releasing records, except in specific cases outlined by law.
In addition to granting access rights, FERPA defines who can request student records. This typically includes parents, eligible students, and, in some cases, other schools requesting records for enrollment purposes.
Protections Provided By FERPA
FERPA provides students and their families with several privacy protections:
Access to Records: Parents and eligible students can request access to education records and review the information they contain.
Consent Requirements: Schools cannot release personal information from a student’s records without written consent, except under limited circumstances such as school transfers, audits, or emergencies involving health or safety.
Disclosure Logs: Schools must keep a record of who has requested or accessed student records, ensuring transparency and accountability.
Who Must Comply?
FERPA applies to any public or private elementary, secondary, or post-secondary school, as well as any state or local education agency that receives funding through programs administered by the U.S. Department of Education.
Schools and agencies covered by FERPA must have policies in place to protect student records and comply with requests for access or corrections.
Compliance Tips:
Track Disclosures: Maintain a record-keeping system to log access requests and disclosures of student records.
Limit Access: Ensure only authorized individuals have access to educational records, and review permissions regularly.
Secure Disposal Practices: Safely destroy outdated records that no longer need to be retained under FERPA guidelines.
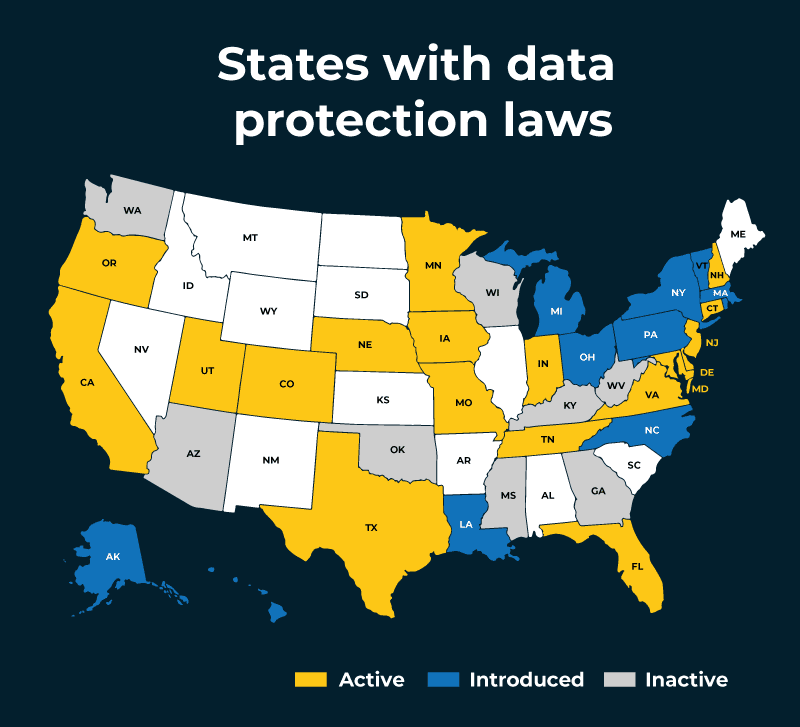
State Specific Data Privacy Laws
Privacy laws at the state level continue to expand as lawmakers respond to growing concerns about data protection. With technology advancing quickly, new state privacy laws were added in 2025 alone, each attempting to address gaps in existing regulations and give consumers more control over their personal information.
While not every proposed bill becomes law, interest in stronger privacy protections is clearly on the rise. So far, 19 states have passed laws granting consumers additional rights, such as the ability to access or delete their personal data and opt out of its sale.
Many of these laws also focus on online privacy. Businesses offering e-commerce services or operating websites often need to provide clear, easy-to-find privacy policies explaining how data is collected, used, and shared.
For businesses operating in multiple states, keeping up with privacy requirements can be challenging since state laws sometimes overlap or differ in key areas. This patchwork approach highlights why many are calling for more comprehensive federal regulations.
Businesses that collect or store PII and PHI should stay informed about state laws that might affect how they manage sensitive data.
The diagram below outlines the current status of privacy laws by state as of January 2025 and can be used as a quick reference.
Data Disposal Laws
Improper disposal of confidential information can lead to data breaches and identity theft. For this reason, more than 35 states have implemented data disposal laws that require entities to take “reasonable measures” to destroy, dispose of, or otherwise make personal information unreadable or indecipherable. These reasonable measures include the “burning, shredding, or pulverizing” of paper documents in a secure manner.
The FTC has also stepped in to protect the privacy of consumer information by issuing its own disposal requirements. The FACTA disposal rule requires proper disposal of information in consumer reports and records to protect against “unauthorized access to or use of the information.” The rule applies to consumer reports or any information derived from consumer reports.
HIPAA also contains provisions that require “covered entities and business associates” to implement safeguards to avoid prohibited use or disclosure of personal health information. This includes policies and procedures to address the final disposal of records that contain PHI. HIPAA also requires that all employees are trained in proper HIPAA compliant data disposal procedures.
Security Breach Notification Laws
All 50 states and U.S. territories have passed laws that require businesses and government agencies to notify individuals of security breaches involving personally identifiable information.
Each state issues its own rules about who must comply with the law, as well as defines what constitutes as personal information, what is considered to be a breach, who should be notified should the breach occur, and the required time-frame of notification.
The NCSL provides a comprehensive list of security breach notification laws by state for reference.
What are the penalties for non-compliance with data privacy laws?
Businesses should be aware of all relevant regulations before they collect any personal information. Failure to comply with data privacy laws can lead to lawsuits and hefty fines.
For example, failure to abide by FACTA may result in stiff penalties. Victims are entitled to the actual damages caused by noncompliance and may also seek statutory damages, and, in some cases, file class-action suits. Federal and state authorities are also authorized to bring legal enforcement actions against businesses that violate the Act.
Violations of HIPAA can also include criminal penalties, including up to ten years imprisonment in certain cases.
States also establish their own consequences for non-compliance with their privacy laws. For example, violations of the California Consumer Privacy Act issues fines of up to U$2,500 per violation or USD 7,500 if the violation was intentional, with no cap on the total amount of fines.
How Can My Business Stay Compliant With Data Privacy Laws?
For businesses that collect or store personally identifiable information, prioritizing data privacy and security is an investment in your business. Protecting sensitive information helps reduce the risk of legal issues, lowers the chances of a data breach, and builds trust with your customers.
Even if your business isn’t specifically required to comply with certain privacy laws, following best practices for data protection can go a long way toward minimizing risk and improving security.
Staying compliant, however, can be challenging without dedicated resources. That’s why many businesses partner with third-party providers to simplify data management and security.
At SecureScan, we make compliance with data privacy laws easier by providing secure document scanning services that meet even the most stringent requirements. Digitizing paper records helps businesses improve data security, streamline access to information, and establish a clear chain of custody for sensitive data.
We also offer FACTA and HIPAA-compliant shredding services for businesses that need a secure way to dispose of outdated paper records. Each shredding service includes a certificate of destruction to verify compliance with legal standards.
Contact us today to learn more about how we can help you meet your data privacy obligations, or request a free scanning quote from one of our scanning technicians who can answer your questions and guide you through the process.
